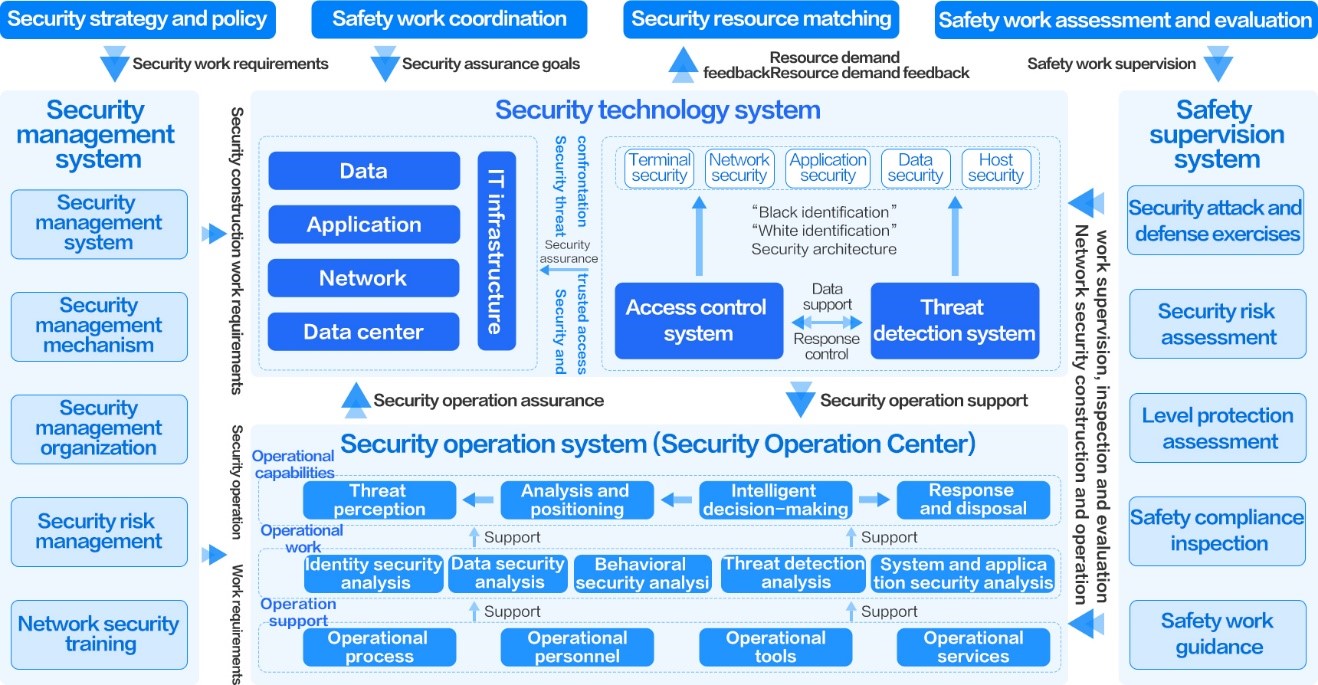
Complete access control
A complete internal and external access control system has been established based on the zero-trust control center, and access behaviors are continuously monitored and adjusted to build a unified identity authentication system for the entire network.
1. The network partitioning and zoning are further refined, the export firewall is redundant, and the reliability is further improved.
2. Before internal/external network access users access the network, terminal security baseline checks and access capabilities have been added.
3. For internal/external network access users in the network, the ability to perform identity-based access control, continuous monitoring of user behavior, and dynamic reduction of access rights have been added to assist customers in smoothly transitioning to a zero-trust architecture.
4. Added network-wide device log auditing to record every access process for easy post-audit and tracing
5. Unified identity authentication platform realizes one-time authentication and full network access
Accurate threat detection system
1. The cloud (XDR) + network (situation) + terminal (EDR) all-round threat inspection system greatly reduces false alarms , improves the accuracy of threat monitoring, and completely traces the attack chain.
2. Cloud, network, and terminal linkage event handling reduces the difficulty of closing the loop of security incidents, and relies on the cloud-based XDR platform capabilities to expand the ability to obtain threat intelligence and synchronize similar security incidents across the country.
Security Monitoring and Operations
1. The cloud-based "platform + people" is used to achieve 7*24 hours of uninterrupted security incident monitoring and handling.
2. Proactively identify and resolve problems, optimize the network security system, and achieve proactive defense.
3. The security perception management platform SIP integrates the two major scenario capabilities of "security operation" and "advanced threat detection", aiming to build a big data intelligent security analysis platform for users that integrates detection, visualization, and response, making network security perceptible and easy to operate, and quickly linking security incidents in a closed loop.